These training resources will prepare an IT Support Representative with the knowledge they need to use BeyondTrust (formally Bomgar) effectively and efficiently. If you would like to schedule one-on-one or group training with a Remote Support Administrator, please contact Nick Merchen or Raul Ochoa.
Remote Support at Nebraska
Remote Support at the University of Nebraska has been architected with user privacy and data security as the foundation. All data transmitted during a remote session is encrypted from end to end, and all actions performed by IT staff during a support session are logged and routinely audited. Users are always in full control of their support experience when connecting with an IT support representative. On privately issued University devices, local user consent is required to begin the remote session and allow an IT support representative to access and control the device. At any time a user can terminate the remote session by closing the BeyondTrust chat window.
Session Configuration
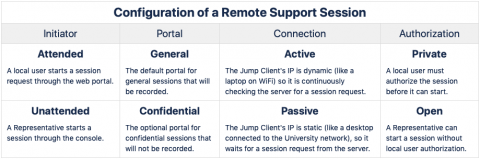
The configuration for a Remote Support session is determined in four phases: Initiator, Portal, Connection, and Authorization.
Phase 1 - Session Initiator
A support session is initiated by a user or a Remote Support Representative.
Attended
Attended sessions are initiated by a local user that navigates to one of two online portals: help.nebraska.edu or help-confidential.nebraska.edu. At the support portal, a user selects the name of their IT Support Representative or the user types in a pre-shared session key. This method of remote support requires a user to download and install a temporary Jump Client. The user must accept a Remote Support EULA before support can start. The user is in full control of the support session and can terminate it at any time. After the session is complete, the temporary Jump Client automatically uninstalls.
Unattended
A Remote Support Representative initiates an unattended session through the console on endpoints that have a pre-installed Jump Client. This method of remote support does not require a user to install anything or take any action to begin remote support. The user will be presented with a Remote Support EULA in the chat window that appears when a support session starts. A local user is in full control of the support session and can terminate it at any time. Only University issued endpoints may have permanently installed Jump Clients.
Phase 2 - Session Portal
Remote Support Sessions flow through one of two session portals.
General Portal – help.nebraska.edu
The general support portal is for regular remote support sessions. General sessions are recorded for training and quality control purposes. Session recordings and logs will be retained for 90 days.
Confidential Portal – help-confidential.nebraska.edu
The confidential support portal is for remote support sessions that will involve confidential or regulated information. Confidential sessions are not recorded, only basic session metadata will be logged for training and quality control purposes. Session logs will be retained for 90 days.
Unattended Jump Clients are pre-configured to use the General or Confidential portal during installation.
Phase 3 - Session Connection
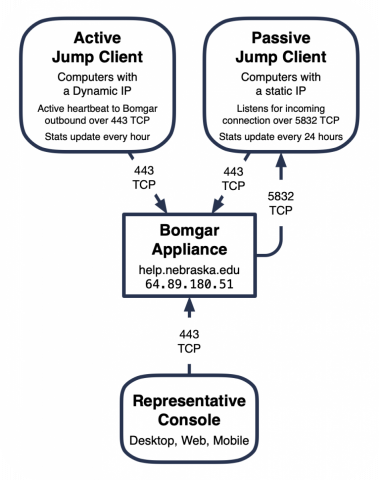
Standard BeyondTrust Remote Support Sessions operate through Jump Clients. Jump Clients are available for Windows, Mac, or Linux endpoints, as well as Android phones and tablets. Pre-installed Jump Clients are accessed from any of the Remote Support Representative consoles. Jump clients can be mass deployed through SCCM and Jamf Pro or installed manually. To locate specific endpoints in the console Jump Clients are organized into groups and can then be individually marked with tags or comments. After receiving Representative access, Jump Client downloads will be available from Box.
Two types of Jump Clients are deployed to University endpoints, Passive and Active.
Passive
Passive clients listen for session requests. The Passive client will listen over TCP 5832 and wait for a session call which happens over TCP 443. Once the call is initiated from the BeyondTrust appliance, the Passive client establishes a session over TCP 443. When the session ends, the Passive client returns to a listening state on TCP 5832. Passive clients check in to the BeyondTrust appliance every 24 hours to update inventory.
Passive clients are best suited for endpoints that have a static network address and are accessible over TCP 5832. Local and network firewalls will need to allow incoming traffic over TCP 5832 for a Passive client to function.
Active
Active clients maintain a heartbeat with the BeyondTrust appliance. Active clients continuously check in with the BeyondTrust appliance looking for session requests over TCP 443 and log their current status and network location. When a Remote Support Representative initiates a support session the Active client will see the request and establish a session. When the session ends, the Active client returns to a regular heartbeat. Active clients will submit inventory information every hour.
Active clients are best suited for mobile endpoints or those without a static address. Local and network firewalls do not require modification for an Active client to function. Active clients generate more network traffic and place a substantial load on the server, for this reason, they are only deployed to devices when needed.
If any Passive or Active Jump Client is offline for more than 30 days, the Representative Console will mark the Jump Client as "Lost" until a connection is re-established. If the device remains offline for 120 days, the Jump Client will be removed automatically from the Representative Console and the device.
Phase 4 - Session Authorization
Remote Support Sessions use one of two permission configurations for the Representative.
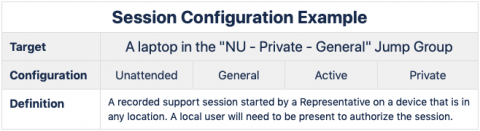
Private
This access role is for accessing Unattended private institutional endpoints or one-time Attended endpoints.
A private institutional endpoint is defined as any desktop, laptop, or tablet that is assigned to a single user for their private use. Examples of private institutional endpoints are those assigned to individual Faculty, Staff, and Students.
A pre-installed Jump Client on private institutional endpoints makes remote assistance quick and easy for users by enabling a Representative to initiate a remote session after being contacted by a user for assistance. Users must be present to accept the remote session and elevate representative access. The user is in full control of the support session and can terminate it at any time.
Open
This access role is for accessing non-private institutional endpoints.
A non-private institutional endpoint is defined as any desktop, laptop, tablet, or server that is not assigned to a single user and does not contain private user data. Examples of non-private institutional endpoints include research or business workstations, lab computers, appliances, kiosks, digital signs, and servers.
A pre-installed Jump Client on non-private institutional endpoints allows Representatives to openly connect to and control these endpoints without local user presence. This role is useful for managing end-user endpoints that do not contain private or confidential information or administering servers. Open Unattended Jump Clients will not be configured to use the Confidential Portal.
Session Configuration Summary
These diagrams summarize the different ways a Remote Support session at the University of Nebraska functions. If you have any questions about Session Configuration, please contact Nick Merchen.
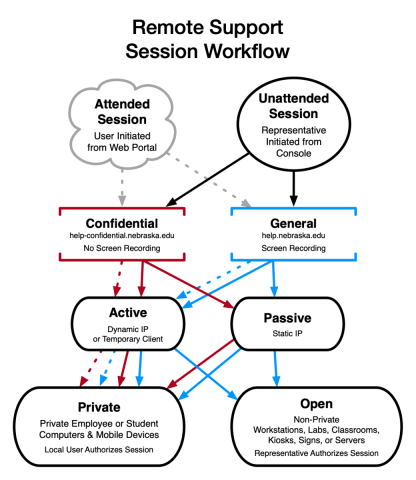
All Private Unattended Jump Clients reside within common Jump Groups in the Remote Support Representative Console. Open Unattended Jump Clients are divided into separate private Jump Groups based on Representative privileges for specific IT support teams. Only one Open Unattended Jump Group will be allocated per IT support team.
Open Unattended Authorization for Private Endpoints
Colleges & Departments can opt-in their private institutional computers to Open Unattended access by completing an Open Unattended Authorization for Private Endpoints Memorandum of Understanding (MOU).
NU-ITS Remote Support policy protects end-user privacy with restrictions on how private institutional computers can be accessed through BeyondTrust. By default, Representatives access private institutional computers through the General Attended or Private Unattended access roles. The Open Unattended Authorization for Private Endpoints MOU authorizes the use of the Open Unattended access role on private institutional computers for a specific College/Department.
When requesting an MOU, please provide the following information. The Dean or Director of the College/Department that will be accepting the MOU and a definition of the Private institutional computers that are in scope of the requested MOU. Only one Open Unattended Jump Group will be provisioned per IT Support team.
Once you have this information, please send it to Phil Redfern. A brief meeting will be scheduled with the Dean/Director of the College/Department to review the agreement and sign the MOU. All agreements will require the approval of ITS Assistant Vice Presidents of Client Services and Security.
Representative Console
Remote Support licensing is provided as concurrent use for active Representatives. Remote Support Representatives should only open the console as needed to facilitate a remote session, then promptly log-off when the session is complete. If a Representative leaves the console idle for 15 minutes, he or she will be automatically logged out.
Desktop Console
To use the Desktop Console, you will need to download and install it from help.nebraska.edu/login. Authentication uses SAML with your TrueYou Identity and DUO two-factor authentication. If you don't know your TrueYou Identity or have not yet enabled DUO, please visit the TrueYou Identity Manager.
Optional Web Browser Configuration
When you log into the Remote Support Representative Console using SAML, you will be redirected to the TrueYou Single Sign-On page for authentication on your default web browser. Following authentication, a BRCS file is downloaded to your default download location, and you must 'launch' the file to complete the Remote Support Representative Console launch process. As long as the default web browser remains open after the initial login, you should not be redirected to the TrueYou SSO page for subsequent logins, though the BRCS file will need to be opened for each login. Here are some configuration options for opening the BRCS file automatically for the 4 most common web Browsers.
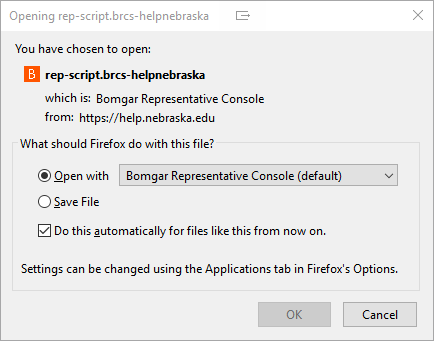
Firefox
When the file is finished downloading, a dialog box will appear, and you can select the following options.
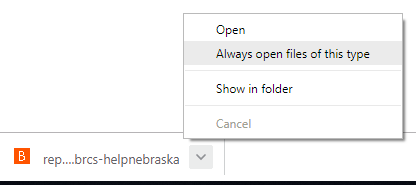
Chrome
When the file is finished downloading, click the "V" next to the file name and select "Always open files of the type" and then open the file.
Safari
Download and install the NU-BomgarRepConsole-AutoLaunch package to configure your Mac to launch the BRCS file automatically, when using Safari.
Edge
When the file is finished downloading, click the "Open" button in the dialog bar at the bottom of the browser screen. Currently, there is not a way to automate opening this file in Edge.
SAML Desktop Console Login Walkthrough
Watch or Download the SAML Desktop Console Login Walkthrough Video Here.
Web Console
The Web Console is HTML5 and works on most modern browsers. While it does not provide the full set of features available in the Desktop Console, all essential functions are available for remote support.
- Web Console Guide
- Web Console Requirements
- Launch the Web Rep Console
- View Sessions in Queue
- Support Session Actions
Mobile Console
The Mobile Consoles provides the majority of remote support features available in the Desktop Console. To use a Mobile Console, you will need to download the appropriate App for your OS.
Support Sessions
Public Sites
Attended Walkthrough
Watch or Download the Attended Walkthrough Video Here.
- Confidential Portal
Persistent Jump Clients
Private Unattended Walkthrough
Watch or Download the Private Unattended Walkthrough Video Here.
Open Unattended Walkthrough
Watch or Download the Open Unattended Walkthrough Video Here.
Other Jump Methods
In addition to Jump Clients, the Remote Support Desktop Console supports traditional Microsoft RDP and VNC sessions. Both of these session types are initiated locally and may require a VPN to access endpoints behind firewalls. A Representative can save a private list of RDP and VNC shortcuts for rapid use at any time.
BeyondTrust enhances RDP and VNC by enabling collaboration with the same external Representative Invite used on Jump Clients. An RDP session can be shared with anyone using a modern web browser. Both RDP and VNC sessions are logged and recorded similar to a standard Jump Client session.
Mobile Device Support
BeyondTrust provides support for iOS and Android mobile devices with features that include chat, screen sharing, file transfer, specifications, and remote control on some Android devices. Another unique feature for mobile devices is BeyondTrust Insight, giving a user the ability to share their device camera remotely with Representative.
Session Tools
BeyondTrust offers powerful session tools that make remote support better than being physically at the endpoint.
- Session Toolset
- Chat Features
- Screen Sharing
- Multi-Monitor Support
- Annotations
- File Transfer
- Command Shell
- System Information
- Registry Access
- Show Screen to Client
- Share Session with Other Representative
- External Representative Invite
Reporting
Remote Support automatically records all session activity, real-time monitor activity (excluding the Confidential Portal), and produces a detailed log for auditing. Recordings are also useful tools for training and presentations.
Reporting Walkthrough
Watch or Download the Reporting Walkthrough Video Here.
Remote Support Training Session
This recording of the Remote Support training session given on December 20th, 2018 presents many of the basic functions of the BeyondTrust support tool.
Remote Training Session
Watch or Download the Remote Training Session Video Here.

